Enhancing Cybersecurity with Conditional Access Policies

As organizations embrace cloud services and remote work to fuel business growth, they must reassess conventional security measures to safeguard sensitive data, applications and resources. Microsoft Azure Active Directory (Azure AD) offers Conditional Access as a powerful security solution, allowing companies to control access through user identity, device, location and other contextual variables. This blog delves into Conditional Access policies, examines their significance for cybersecurity and discusses how they can enhance an organization’s security posture.
Understanding Conditional Access Policies
Conditional Access policies, at their most basic, are if-then statements; if a user desires to access a resource, they must complete an action. Example: A remote employee wants to access the company’s intranet portal and is required to connect through a secure VPN.
Conditional Access policies are rules and conditions within Azure AD that help organizations manage access to resources, applications and data. They enable administrators to enforce granular access controls based on the user’s access requests context, such as their device, location or risk level. The policies consist of several components, including assignments that specify the users, groups and applications to which a policy applies. Conditions determine the circumstances for policy enforcement, while access controls define the actions taken when a policy is triggered.
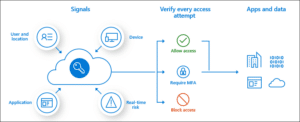
Once first-factor authentication is complete, the system applies Conditional Access policies. While Conditional Access does not serve as an organization’s first line of defense for scenarios like denial-of-service (DoS) attacks, it can utilize signals from these events to determine access. – Microsoft
Importance for Cybersecurity
Conditional Access improves an organization’s cybersecurity posture for several reasons:
- Context-Aware Security – By considering user identity, device and location factors, organizations can make informed decisions about granting access and minimizing the risk of unauthorized access to sensitive data.
- Adaptive Authentication – Implementing adaptive authentication mechanisms, like multi-factor authentication (MFA) when necessary, provides an additional security layer, especially during access to crucial resources, by adjusting authentication requirements based on contextual factors such as user behavior, device, location, time and other risk indicators.
- Simplified Management – Azure AD’s centralized management console allows administrators to easily create, modify, and enforce organizational policies. This ability streamlines the process of managing access controls and reduces the likelihood of misconfigurations or security gaps.
- Compliance Assurance – Organizations with strict compliance requirements can enforce specific access controls for regulated data and applications, thus meeting regulatory obligations and reducing the risk of fines or penalties.
- Improved User Experience – Dynamically enforcing access controls based on context helps balance security and usability, allowing users to access resources seamlessly while protecting sensitive data and systems.
Implementing Conditional Access Policies in Your Organization
To effectively deploy Conditional Access policies within your organization, start by assessing security needs. Identifying critical applications, data and resources requiring enhanced security helps prioritize the policies to create and apply.
Next, establish access requirements for each sensitive resource, taking into account factors such as user roles, device compliance and geographic location. Create Conditional Access policies based on the defined requirements and test them in a controlled environment before deploying them across the organization. This approach ensures the policies function as intended and do not inadvertently disrupt access for legitimate users.
Regularly monitoring and adjusting your policies is essential to address new risks, changes in the threat landscape or evolving business requirements. Additionally, educating users is crucial. Inform them about the importance of Conditional Access policies and their role in resource protection. Encourage users to follow best practices for secure access, such as using MFA, keeping devices up-to-date and reporting suspicious activity.
Finally, integrate Conditional Access policies with other security solutions in your organization, such as threat intelligence, data loss prevention (DLP) and identity and access management (IAM) tools. This integration delivers a more comprehensive security approach.
Break the Glass Account
A “Break the Glass” account is an emergency account created within an organization’s IT environment to ensure continued access to critical systems and resources in case of unforeseen events. These emergencies could include a significant security incident or a misconfiguration in Conditional Access policies. These accounts must be created with highly privileged access and strong security controls.
The necessity of a Break the Glass account when using Conditional Access lies in the possibility of accidentally locking out administrators or users from essential resources, applications or services due to policy misconfigurations or unexpected changes in the organizational environment. In such situations, the Break the Glass account serves as a failsafe that allows designated personnel to regain access and rectify the issue, ensuring business continuity and minimal disruption. These accounts are also crucial to an effective incident response plan, enabling organizations to respond quickly to and recover from security breaches or other critical incidents.
Final Thoughts on Conditional Access Policies
Conditional Access is a basic and necessary component of modern cybersecurity strategies. By implementing context-aware access controls and adaptive authentication mechanisms, organizations can balance security and usability, allowing users to access resources when needed while protecting sensitive data and systems. As a fundamental aspect of access management, Conditional Access policies should be a priority for organizations looking to strengthen their security infrastructure.
While Conditional Access policies effectively help combat cyberattacks, they are only one aspect necessary to protect your data. OneNeck understands a holistic approach to security is essential for protecting your organization and its precious resources. As a skilled IT security services provider, we are here to help. Our team can assess your security posture, develop a protection strategy and help better leverage your security investments.
Contact us today to speak with a OneNeck security professional.
![]()
